SSH Tunneling » History » Version 5
« Previous -
Version 5/6
(diff) -
Next » -
Current version
sph, 08/23/2010 05:57 PM
SSH Tunneling¶
This is more of a quick howto for those who are already somewhat familiar with SSH tunneling. For more detailed information about SSH tunneling you can check your SSH client's manpage.
There are two ways to tunnel your client-core connection over SSH. You can either use static port forwarding or use a socks5 proxy.
Static port forwarding¶
Forward local port 4242 to the correct on the core machine:
$ ssh -L 4242:localhost:4242 example.com
The same can be achieved via PuTTY by entering 4242 as source port and localhost:4242 as destination in the SSH > Tunnels tab.
In the client simply connect to localhost, port 4242.
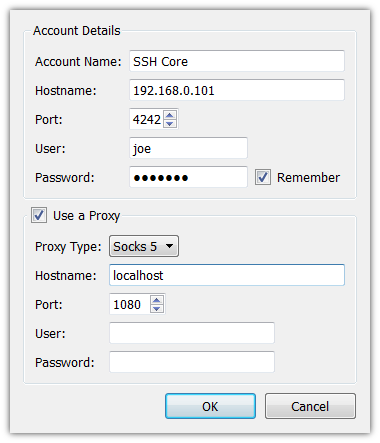
Socks 5 proxy¶
Modern SSH clients like OpenSSH and PuTTY can also use dynamic port forwarding by turning itself into a socks proxy. Quassel can then set up a connection to the core using this proxy.
$ ssh -D 1080 example.com
In PuTTY, you can select the Dynamic option and then add 1080 in the SSH > Tunnels tab.
Now the client setup is a little bit more difficult since Qt 4.5 and earlier do not support hostname forwarding so you will need to figure out the local IP address of the core because connecting to 127.0.0.1 or localhost will not work for now.
Here is an example configuration: